Selamat datang, esteemed readers, to a deep dive into the realm of mobile app management solutions. These solutions, crucial for today’s dynamic business landscape, are designed to streamline and secure mobile app deployments. From intricate configurations to robust security measures, these solutions are more than just tools; they are strategic assets that elevate productivity and protect valuable data.
Understanding the various aspects of mobile app management is paramount for businesses of all sizes. This comprehensive overview will explore the key features, benefits, and considerations when choosing the right solution for your specific needs. We will delve into the intricacies of security, device management, and the ever-evolving landscape of mobile technology.
Introduction to Mobile App Management (MAM) Solutions

Mobile App Management (MAM) solutions are indispensable tools for organizations seeking to control and optimize their mobile device deployments. They offer a centralized platform for managing, securing, and monitoring mobile applications across various devices, ensuring compliance and productivity. A robust MAM solution is crucial for businesses to effectively manage the growing complexity of mobile environments.
Effective mobile app management is no longer a luxury but a necessity. The increasing reliance on mobile devices for business operations necessitates a structured approach to app deployment, security, and usage. MAM solutions provide the critical framework for achieving this control, ultimately streamlining workflows and safeguarding sensitive data.
Definition of Mobile App Management (MAM)
Mobile App Management (MAM) is a comprehensive platform designed to centrally manage, secure, and monitor mobile applications across a diverse range of devices. It encompasses policies and procedures for deployment, updates, usage, and security of applications on employee devices. MAM systems are tailored to offer a structured approach to mobile device and application management, facilitating compliance and productivity.
Core Functionalities of a MAM Solution
MAM solutions encompass a range of functionalities crucial for modern mobile environments. These include: application deployment and management, security policies, device management integration, usage monitoring, and reporting. A robust MAM system allows for granular control over app access, updates, and usage, enabling organizations to tailor policies to specific needs and maintain compliance with regulations.
Types of Mobile Apps Managed by MAM Solutions
MAM solutions are not limited to a single type of application. They effectively manage a broad spectrum of mobile applications, including business-critical applications, productivity tools, and even entertainment apps used for employee engagement. The ability to manage a wide range of apps is a critical component of a successful MAM strategy.
Industries Where MAM Solutions are Crucial
MAM solutions are essential in numerous industries where mobile devices are integral to operations. Examples include healthcare, finance, retail, and government. In healthcare, MAM is critical for maintaining patient data security and regulatory compliance. In finance, MAM solutions ensure the security of sensitive financial transactions and data.
Comparison of MAM Solution Categories
| Category | Description | Pros | Cons |
|---|---|---|---|
| Cloud-Based | MAM solutions hosted and managed by a third-party provider. | Scalability, accessibility, cost-effectiveness for smaller organizations, rapid deployment, centralized management. | Vendor lock-in, potential security concerns (depending on the provider), reliance on internet connectivity. |
| On-Premises | MAM solutions hosted and managed on the organization’s own servers. | Greater control over data security, customization options, potentially better integration with existing infrastructure. | Higher initial investment, ongoing maintenance costs, limited scalability, reliance on IT resources. |
Cloud-based MAM solutions provide an accessible and scalable solution for managing mobile apps, while on-premises MAM solutions offer greater control and security. The optimal choice depends on the specific needs and resources of the organization.
Key Features and Capabilities of MAM Solutions
Mobile Application Management (MAM) solutions are critical for organizations to effectively manage and secure mobile devices and applications. Robust MAM solutions are essential for modern businesses navigating the complexities of a mobile-first world. Their core function is to control, monitor, and secure the mobile landscape, protecting sensitive data and maintaining compliance standards. Failure to implement a strong MAM strategy can lead to significant security vulnerabilities and regulatory breaches.
Essential Features of Top-Tier MAM Solutions
Top-tier MAM solutions are distinguished by a comprehensive set of features designed to address the specific needs of modern enterprises. These solutions go beyond basic device management, offering granular control over application deployment, security, and compliance. The most crucial features include detailed device profiling, application provisioning, and comprehensive reporting mechanisms.
Security Features within MAM Solutions
Security is paramount in MAM solutions. Robust security features are critical for protecting sensitive data from unauthorized access and malicious attacks. Advanced encryption, secure remote wipe capabilities, and granular access controls are fundamental elements. The ability to enforce strong password policies, and restrict access to sensitive applications based on user roles are vital. Effective security measures prevent data breaches and maintain the integrity of sensitive company information.
Role of Compliance Features in MAM Solutions
Compliance is another critical function of MAM solutions. They must align with industry regulations and company policies, enabling organizations to ensure compliance with relevant standards. MAM solutions should automate the enforcement of compliance policies and allow for audit trails to track compliance status. This functionality helps prevent regulatory penalties and maintain a positive reputation.
Integration with Existing IT Infrastructure
Seamless integration with existing IT infrastructure is a key differentiator for successful MAM deployments. Solutions should integrate with existing identity management systems, allowing for single sign-on capabilities and unified access management. Integration with existing MDM (Mobile Device Management) systems can further streamline the mobile management process. A successful integration avoids redundant tools and workflows, ensuring a smooth transition to a unified mobile management strategy.
Importance of Reporting and Analytics within MAM Solutions
Comprehensive reporting and analytics are vital for effective mobile device management. MAM solutions should provide real-time insights into device usage, application performance, and security events. Detailed reporting allows for proactive identification of potential issues and ensures that administrators can respond swiftly to security incidents. This proactive approach facilitates informed decision-making and optimized resource allocation.
MAM Features and Benefits
| Feature | Benefit |
|---|---|
| Device Inventory and Management | Provides a complete view of all mobile devices, enabling granular control over settings, applications, and security policies. |
| Application Management | Facilitates the deployment, configuration, and management of mobile applications, ensuring controlled access and compliance. |
| Security Policies | Enforces security policies to protect sensitive data, ensuring data encryption and access restrictions. |
| Compliance Reporting | Provides detailed reports on compliance status, facilitating regulatory audits and reducing risk of non-compliance penalties. |
| Integration with Existing Infrastructure | Allows seamless integration with existing IT systems, eliminating redundant tools and streamlining workflows. |
| Real-Time Monitoring | Provides real-time insights into device and application activity, allowing for rapid response to security incidents and performance issues. |
Evaluating Mobile App Management Solutions
Choosing the right Mobile App Management (MAM) solution is critical for organizations seeking to secure and manage their mobile applications effectively. A poorly chosen solution can lead to significant security vulnerabilities, increased management overhead, and ultimately, decreased productivity. Thorough evaluation is paramount to ensure the selected solution aligns with the organization’s specific needs and future growth trajectory.
A robust evaluation process requires a multifaceted approach, considering factors beyond basic functionality. This includes scrutinizing vendor support, deployment complexity, scalability, and the overall fit with existing infrastructure and processes. Only by understanding the strengths and weaknesses of different solutions can organizations make informed decisions and avoid costly mistakes.
Comparing and Contrasting MAM Solutions
Different MAM solutions cater to various organizational needs and budgets. Some solutions excel in specific areas, like security or compliance, while others offer a broader range of features. For example, a solution focused on enterprise mobility management (EMM) may offer more comprehensive device management capabilities, but a dedicated MAM solution might focus on granular app control and security policies. Evaluating the specific strengths and weaknesses of each solution is crucial in selecting the best fit.
Criteria for Evaluating Suitability
A suitable MAM solution must meet the specific requirements of the organization. Key criteria include the number of mobile devices in use, the types of applications deployed, and the organization’s security policies and compliance standards. For instance, an organization with a large, geographically dispersed workforce may require a solution with robust remote management capabilities. Similarly, a company handling sensitive data may prioritize solutions with advanced data encryption and access control features.
Evaluating Scalability
MAM solutions must be scalable to accommodate future growth. Factors to consider include the anticipated increase in mobile devices, applications, and user base. A solution that struggles to handle growing demands can quickly become a bottleneck, leading to performance issues and increased management overhead. Organizations should thoroughly investigate the solution’s ability to adapt to changing needs and avoid potential limitations in the future. Consider how the solution handles concurrent user access and the ability to add new features without significant disruption.
Importance of Vendor Support
Vendor support plays a vital role in the success of any MAM solution. A strong support team can provide timely assistance during implementation, troubleshooting issues, and training users. Evaluate the vendor’s reputation for responsiveness, the availability of different support channels (phone, email, ticketing system), and the quality of documentation. A solution with inadequate support can lead to significant delays and increase operational costs.
Assessing Ease of Deployment and Management
A user-friendly interface and clear documentation are essential for seamless deployment and ongoing management. The solution should be intuitive for administrators to configure, manage, and maintain. Consider the time required for implementation, the complexity of configuring policies, and the ease of troubleshooting common issues. A solution that is difficult to deploy or manage can negatively impact efficiency and introduce additional costs.
Evaluation Criteria Table
| Evaluation Criteria | Description | Importance |
|---|---|---|
| Security Features | Data encryption, access controls, and threat protection | Critical for sensitive data protection |
| Scalability | Ability to handle increasing device and app counts | Essential for future growth |
| Integration with Existing Systems | Compatibility with existing infrastructure and tools | Reduces integration overhead |
| Vendor Support | Responsiveness and quality of support resources | Crucial for troubleshooting and maintenance |
| Deployment Complexity | Ease of implementation and configuration | Impacts time to value |
| Management Interface | Intuitiveness and usability of the admin console | Affects operational efficiency |
| Cost | Total cost of ownership, including licensing, support, and training | Critical for budget planning |
Mobile App Management Solutions in Different Environments
Mobile App Management (MAM) solutions are no longer a luxury but a necessity for businesses of all sizes and industries. Their adaptability to diverse operational models and regulatory environments is crucial for maintaining security, productivity, and compliance. Effective MAM solutions are pivotal in streamlining mobile device management, ensuring data security, and ultimately improving overall operational efficiency.
MAM solutions are strategically designed to address the unique needs of different business models, industries, and regulatory landscapes. They offer a powerful framework for businesses to leverage the advantages of mobile technology while mitigating associated risks. By providing comprehensive control and visibility across all mobile devices and applications, MAM solutions are a crucial investment for modern organizations.
Adaptability to Diverse Business Models
MAM solutions demonstrate remarkable flexibility, seamlessly integrating into various business models, including remote work environments. This adaptability is critical for maintaining operational continuity and security in distributed workforces. For instance, MAM solutions can be configured to enforce access policies based on location, device type, or user role, ensuring sensitive data remains protected regardless of employee location. This flexibility allows businesses to quickly adapt to changing needs, ensuring that MAM solutions are not just reactive but proactively support their evolving operational models.
Addressing Specific Industry Needs
MAM solutions are specifically designed to address the unique security and compliance requirements of various industries. For example, healthcare organizations require solutions that meet stringent HIPAA regulations, ensuring patient data is protected. Financial institutions need robust solutions to meet stringent regulatory compliance requirements for handling sensitive financial data. Retail organizations can benefit from solutions that manage employee access to sensitive customer information. These industry-specific considerations highlight the importance of selecting a MAM solution tailored to the unique demands of each business.
Considerations for Regulated Environments
Implementing MAM solutions in regulated environments demands meticulous planning and adherence to strict guidelines. This necessitates careful consideration of data privacy regulations (e.g., GDPR, CCPA) and industry-specific compliance standards. Solutions must be thoroughly vetted for their compliance with relevant regulations, and stringent security protocols must be implemented to protect sensitive data. Failure to adhere to these guidelines can lead to severe penalties and reputational damage.
Improving Employee Productivity with MAM
MAM solutions significantly contribute to employee productivity by streamlining workflows and enhancing access to essential resources. By centralizing application management and device control, MAM solutions allow for efficient deployment and management of applications, eliminating the need for manual configuration. This centralized control also allows for granular access policies, enabling administrators to control which applications and data employees can access based on their roles and responsibilities. These features, in turn, promote a more efficient and secure work environment, contributing directly to improved productivity.
MAM Solutions for Different Business Sizes
| Business Size | MAM Solution Considerations | Typical Features |
|---|---|---|
| Small Businesses | Cost-effectiveness, ease of use, and basic security features are paramount. | Simplified deployment, limited user management, basic reporting capabilities, and integration with existing IT systems. |
| Medium-sized Businesses | Scalability, robust security features, and the ability to manage a growing number of devices and applications are crucial. | Advanced user management, reporting capabilities, enhanced security features, and the potential for integration with other business applications. |
| Large Enterprises | Comprehensive security, granular control over applications and devices, and sophisticated reporting and analytics are essential. | Advanced security features, comprehensive user management, extensive reporting and analytics, and the ability to integrate with existing enterprise systems. |
MAM solutions must be carefully chosen to align with the specific needs of each business size. The table above highlights the key considerations and typical features for different business sizes, demonstrating the importance of selecting a solution that effectively meets the requirements of the organization.
Mobile App Security and MAM Solutions
Mobile Application Management (MAM) solutions are crucial for bolstering mobile app security in today’s increasingly mobile-centric business environments. Effective MAM solutions are not just about managing apps; they are a vital component in safeguarding sensitive data and maintaining operational integrity. By implementing robust security protocols and device management strategies, organizations can mitigate risks and ensure the safety of their mobile assets.
Role of MAM Solutions in Securing Mobile Apps
MAM solutions play a pivotal role in securing mobile applications by providing a centralized platform for managing and controlling access to them. This centralized control allows for consistent security policies across all devices and applications, reducing the risk of vulnerabilities. They enable organizations to enforce security policies and prevent unauthorized access to sensitive data.
Security Protocols and Encryption Methods Used by MAM Solutions
MAM solutions leverage various security protocols and encryption methods to protect mobile applications and the data they handle. These include Transport Layer Security (TLS) for secure communication, data encryption at rest and in transit to safeguard confidential information. Advanced encryption standards like AES-256 are frequently implemented to ensure data confidentiality. Strong authentication mechanisms, including multi-factor authentication (MFA), are also crucial components for securing access to applications.
Importance of Device Management in Mobile App Security
Device management is integral to mobile app security. MAM solutions enable organizations to control and monitor the devices used to access their applications. This includes the ability to enforce security policies on devices, such as restricting access to certain apps or requiring specific security configurations. Furthermore, device management allows for remote wiping of data in case of loss or theft, significantly reducing the risk of sensitive information falling into the wrong hands. This control extends to managing operating system updates, software installations, and other aspects crucial to maintaining a secure environment.
Role of Access Control in Securing Mobile Apps with MAM
Access control is a cornerstone of mobile app security within MAM solutions. MAM solutions allow granular control over who can access specific applications, features, and data within those applications. This granular control is crucial in maintaining a high level of security, as it ensures that only authorized personnel can access sensitive data and functions. Implementing role-based access control (RBAC) allows for the creation of different user roles with varying levels of access privileges, streamlining management and enhancing security.
Managing App Permissions Within a MAM Solution
MAM solutions provide tools for managing app permissions effectively. This includes the ability to restrict or grant access to specific data sources, functionalities, and resources within an application. By precisely controlling app permissions, organizations can limit the potential damage caused by malicious or compromised applications. Furthermore, the ability to revoke permissions remotely in case of suspicion or compromise significantly enhances security posture.
Security Features in Different MAM Solutions (Table)
| MAM Solution | Data Encryption | Device Management | Access Control | App Permissions Management |
|---|---|---|---|---|
| Solution A | AES-256, TLS 1.3 | Remote wiping, OS updates, device lockdown | RBAC, multi-factor authentication | Granular control, audit logs |
| Solution B | AES-256, TLS 1.3, FIPS 140-2 | Remote wiping, device posture assessment, app whitelisting | Attribute-based access control, least privilege | Permission policies, automated permission enforcement |
| Solution C | AES-256, TLS 1.3 | Remote wiping, device inventory, patch management | Role-based access control, fine-grained permissions | Customizable permission settings, real-time monitoring |
Note: This table provides a simplified overview and specific features may vary depending on the particular MAM solution.
Mobile Device Management (MDM) and its Relationship with MAM
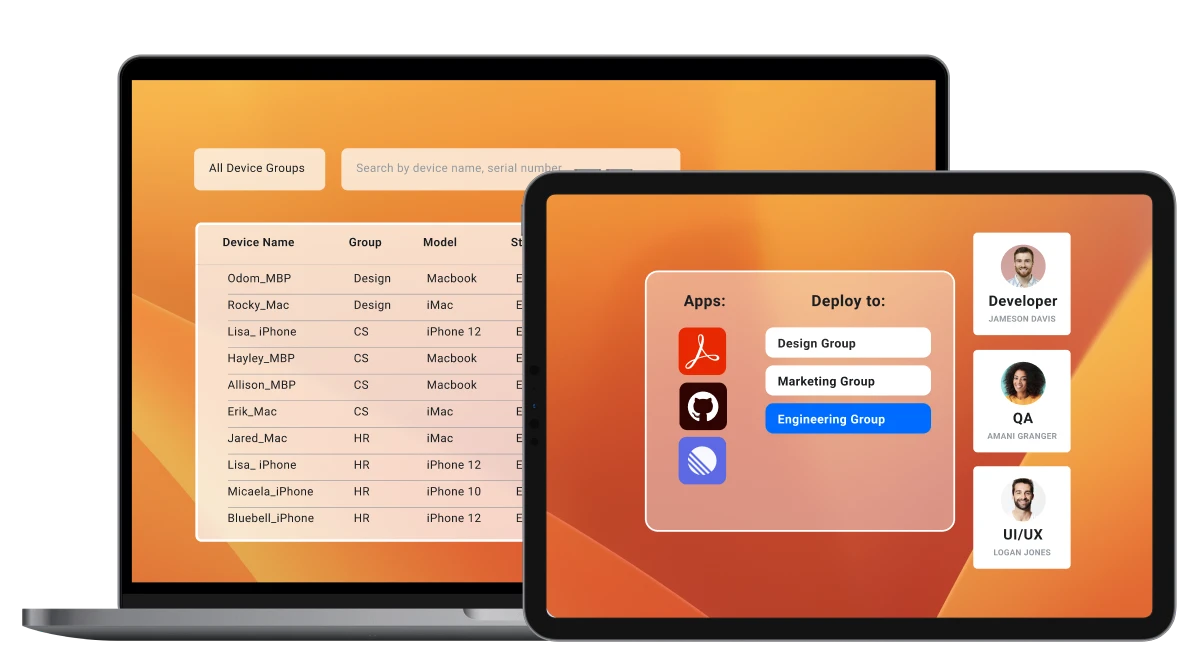
Mobile Device Management (MDM) and Mobile Application Management (MAM) are crucial for securing and managing mobile environments, though they serve distinct but complementary roles. Effective mobile security relies on integrating these solutions, allowing businesses to enforce policies across both devices and applications. A strong understanding of their relationship is vital for maximizing the benefits of each.
MDM and MAM solutions, while distinct, are intertwined in the modern enterprise. MDM primarily focuses on device control, while MAM focuses on application control. However, these are not mutually exclusive; rather, they often work together to achieve comprehensive mobile security. Integrating MDM and MAM solutions offers a more holistic approach to mobile security and management, creating a layered defense against threats.
Relationship Between MDM and MAM Solutions
MDM solutions provide a foundation for managing devices, including configuration, security policies, and access controls. They typically manage the device itself, its operating system, and potentially the installed apps. MAM solutions build upon this foundation by specifically controlling access to and use of applications, ensuring that only authorized apps are used and that data is protected.
Examples of MDM Enhancing MAM Functionalities
MDM solutions can enhance MAM functionalities by:
- Enforcing device security policies, such as encryption and password complexity, which directly impacts the security of applications installed on the device.
- Restricting access to the device, thus limiting access to applications that might be vulnerable or misused.
- Managing device updates, which ensures that applications are running on a secure and updated platform.
- Controlling the installation and removal of apps, preventing unauthorized apps from being installed and thereby affecting MAM policy.
These functionalities are essential for effective mobile security and compliance.
Overlap and Differences Between MDM and MAM
While MDM and MAM solutions share the goal of managing mobile devices and applications, they differ in their scope and focus. MDM is primarily concerned with the device itself, including configuration, security settings, and user access to the entire device. MAM, on the other hand, concentrates on the applications installed on the device, controlling which apps are allowed, their usage, and data access. The overlap lies in the shared goal of securing and managing mobile devices and the applications on them.
How MAM Solutions Leverage MDM Features for Enhanced Security
MAM solutions can leverage MDM features to improve security by enforcing security policies on the device level, thus improving overall security. This includes using MDM to:
- Implement device encryption, which protects the entire device and all data stored on it, including the applications managed by MAM.
- Restrict access to specific applications based on device location or user identity, further enhancing security.
- Ensure device operating systems are updated regularly, thus preventing vulnerabilities that can impact the applications managed by MAM.
These measures are crucial for mitigating security risks.
Use Cases Where Both MDM and MAM Solutions Are Crucial
Businesses that need comprehensive mobile security and management should use both MDM and MAM solutions.
- Financial institutions handling sensitive customer data.
- Healthcare providers managing patient records.
- Government agencies managing classified information.
- Corporations with sensitive business data.
These sectors demand high levels of security and compliance.
Table of MDM and MAM Functions and Capabilities
| Function | MDM | MAM |
|---|---|---|
| Device Configuration | Manage OS, settings, profiles | Application deployment, access |
| Security Policies | Encryption, access control, device wipe | Application usage controls, data protection |
| User Management | User enrollment, provisioning | User access to specific applications |
| Compliance | Device compliance | Application compliance |
This table summarizes the key differences and capabilities of both MDM and MAM solutions.
Deployment and Implementation of MAM Solutions

Effective deployment of a Mobile App Management (MAM) solution is crucial for realizing its benefits. A poorly implemented MAM system can lead to significant operational inefficiencies and security vulnerabilities. Careful planning and execution are paramount to a successful transition.
Deploying a MAM solution requires a phased approach, from initial assessment and planning to ongoing monitoring and maintenance. This process is not a one-time event; rather, it is an iterative process that adapts to the evolving needs of the organization. A robust deployment strategy ensures the solution integrates seamlessly with existing infrastructure and workflows.
Assessment and Planning
A thorough assessment of existing mobile infrastructure, applications, and security policies is essential before implementing a MAM solution. This includes inventorying all mobile devices, applications, and user roles. Understanding current security posture and identifying potential risks associated with mobile devices and applications is vital. A clear understanding of the desired outcomes and goals of the MAM solution is critical. This includes aligning the MAM solution with the organization’s overall security and compliance strategies. This planning phase will dictate the successful deployment of the MAM solution.
Configuration and Customization
Configuring a MAM solution involves setting up policies, rules, and access controls. Customization options should be carefully considered to tailor the solution to the specific needs and workflows of the organization. This includes integrating with existing identity and access management systems. Policies should be created to manage application access, device restrictions, and data encryption. Examples include controlling access to sensitive data, enforcing password complexity, and defining app usage limits. Comprehensive documentation of all configurations is critical for future maintenance and troubleshooting.
Best Practices for Implementation
Implementing a MAM solution requires a phased approach to ensure minimal disruption. Start with a pilot program involving a small group of users and devices to test the solution and identify any potential issues. Conduct thorough training for administrators and end-users. Establish clear communication channels and escalation procedures. Regularly review and update policies and configurations to ensure ongoing effectiveness. Document every step, including configurations and user training.
Ensuring a Smooth Transition
A smooth transition during MAM implementation relies on careful planning and communication. A phased rollout of the MAM solution can minimize disruption to existing workflows. Providing comprehensive training to end-users is essential for their successful adoption of the solution. Clear communication regarding the rollout schedule and any potential impacts on existing processes is vital.
Potential Challenges and Solutions
Implementing a MAM solution can present several challenges. Resistance to change from users and administrators can be mitigated by providing adequate training and support. Integration issues with existing systems can be resolved by careful planning and thorough testing. Scalability issues can be addressed by selecting a solution that can accommodate future growth. Addressing these challenges proactively is key to successful implementation. Implementing a MAM solution is not a quick process, and it requires meticulous planning and execution.
Step-by-Step Guide for MAM Solution Deployment
- Assessment and Planning: Thoroughly assess current mobile infrastructure, applications, and security policies. Define clear goals and desired outcomes.
- Solution Selection: Evaluate and choose the most suitable MAM solution based on your organization’s needs and requirements.
- Pilot Program: Implement the MAM solution on a small group of users and devices to test and refine the configurations.
- Configuration and Customization: Configure policies, rules, and access controls to align with organizational security and compliance strategies.
- User Training: Provide comprehensive training to administrators and end-users on the new MAM solution.
- Phased Rollout: Deploy the MAM solution to different user groups or departments progressively.
- Monitoring and Maintenance: Monitor the performance of the MAM solution and adapt configurations as needed.
Future Trends and Innovations in MAM Solutions
Mobile App Management (MAM) solutions are rapidly evolving, driven by the increasing complexity of mobile environments and the need for robust security and management capabilities. The future of MAM is intrinsically linked to emerging technologies, particularly Artificial Intelligence (AI) and Machine Learning (ML), which promise to revolutionize how organizations manage and secure their mobile apps. This shift demands a proactive approach to adapt and leverage these advancements to stay ahead of evolving threats and maintain a competitive edge.
The core of future MAM solutions will revolve around automation, intelligent analysis, and proactive security measures. AI-powered insights will enable organizations to predict and prevent potential security breaches, streamline deployment processes, and optimize app performance. This evolution is not merely incremental; it’s a fundamental shift in how businesses approach mobile app management.
Emerging Technologies Impacting MAM Solutions
AI and machine learning are poised to transform MAM solutions by automating repetitive tasks, improving security analysis, and personalizing user experiences. These technologies will play a crucial role in identifying anomalies, detecting potential threats in real-time, and adapting to changing user behaviors. The ability of AI to learn from vast datasets will enable MAM solutions to predict and proactively mitigate risks.
AI Transforming Mobile App Management
AI is already demonstrating its potential in transforming mobile app management. Sophisticated algorithms can analyze app usage patterns, identify unusual access attempts, and flag potential security vulnerabilities. For example, AI-powered MAM solutions can detect suspicious login attempts from unusual locations or devices, triggering alerts and implementing security measures. This proactive approach is critical in today’s threat landscape. Further, AI can optimize app deployments, tailoring configurations based on user profiles and device specifications. This personalized approach improves efficiency and reduces operational overhead.
Future Trends in Mobile App Security
Mobile app security will continue to evolve, with an increasing focus on zero-trust security models and behavioral analytics. Zero-trust security mandates that every user and device must be verified before gaining access to sensitive data or resources. This approach is essential in today’s dynamic work environments, where employees may access company resources from various locations and devices. Real-time behavioral analytics will identify anomalies and suspicious activities in app usage patterns, enabling swift responses to threats. This proactive approach is critical for maintaining data integrity and preventing breaches.
MAM Solutions Supporting Remote Work and Hybrid Models
MAM solutions are crucial for managing mobile apps in remote and hybrid work environments. They can provide granular control over access to sensitive applications and data, ensuring compliance with security policies regardless of employee location. Moreover, MAM solutions can facilitate seamless access for employees working from home or in a hybrid setup. Robust device management and access controls are vital to safeguard company resources in these evolving work models.
MAM Integration with Other Business Platforms
The future of MAM solutions hinges on their seamless integration with other business platforms, such as enterprise resource planning (ERP) systems and customer relationship management (CRM) systems. This integration will enable a holistic view of the entire mobile ecosystem, enabling better decision-making and operational efficiency. By connecting MAM with other core systems, organizations can leverage data insights for improved performance and security across all aspects of their operations.
Innovative Uses of MAM Solutions in Specific Industries
MAM solutions can be leveraged in diverse industries to enhance security and operational efficiency. For instance, in healthcare, MAM can ensure compliance with HIPAA regulations while providing secure access to patient data. In the financial sector, MAM can protect sensitive financial information and prevent unauthorized access to banking applications. The tailored capabilities of MAM solutions can adapt to the specific needs of various industries, ensuring compliance and data protection. This adaptation is crucial for maintaining a strong security posture in each industry’s unique environment.
Conclusive Thoughts

In conclusion, choosing the right mobile app management solution is a critical decision for any organization. By carefully evaluating the features, security protocols, and implementation strategies, businesses can ensure optimal performance and compliance. This discussion highlights the importance of these solutions in navigating the challenges and opportunities presented by today’s mobile-first world.





