Navigating Certify compliance can be challenging, but a well-designed mobile app can simplify the process. This guide explores the essential elements of a mobile app for Certify compliance, from defining key features to integrating with existing systems. We’ll cover user experience, security, and development considerations, providing a roadmap for creating a robust and user-friendly app.
Understanding the specific requirements of Certify compliance is crucial for building an effective mobile application. This guide will detail the essential functionalities, security protocols, and user interface design elements to ensure a seamless and efficient compliance experience for all users.
Introduction to Certify Compliance Mobile Apps

Certify compliance mobile apps are crucial tools for streamlining and improving the process of adhering to regulatory standards. These apps empower businesses and individuals to easily manage and track compliance requirements, ensuring adherence to regulations and minimizing potential risks. This streamlined approach to compliance fosters a culture of accountability and transparency.
These apps leverage mobile technology to provide a user-friendly interface for accessing and managing compliance documents, tracking progress, and receiving notifications about updates. This accessibility allows users to stay informed and compliant on the go. A well-designed mobile app can dramatically reduce the administrative burden associated with compliance, allowing users to focus on core business activities.
Key Features and Functionalities
A robust mobile app for certify compliance should offer a range of features to support users effectively. Core functionalities include document management (upload, download, and organization), task management (scheduling and reminders), audit trail capabilities, and secure data storage. Integration with other compliance management systems is essential for seamless data flow. Furthermore, reporting and analytics capabilities help users monitor compliance progress and identify areas needing attention. Finally, the app should be user-friendly, intuitive, and accessible across various devices.
Examples of Successful Mobile Apps in Related Industries
Several successful mobile applications demonstrate the value of this approach in related industries. For instance, several mobile apps in the healthcare industry facilitate the secure exchange of patient information, enabling efficient tracking of medical records and adherence to patient privacy regulations. Similarly, apps in the financial sector support compliance with regulations concerning financial transactions, helping prevent fraud and ensuring regulatory adherence. These examples showcase the potential for mobile apps to improve compliance across a variety of sectors.
Different Types of Users
Several user types will interact with a certify compliance mobile app. These include company employees responsible for maintaining compliance, regulatory agencies needing access to data, and external auditors. Tailoring the app’s features to meet the specific needs of each user group is critical for optimal usage and satisfaction.
Mobile App Platforms Comparison
This table compares different mobile app platforms suitable for certify compliance apps. Choosing the right platform is crucial for functionality, security, and scalability.
| Platform | Pros | Cons |
|---|---|---|
| React Native | Cross-platform development, reduced development time and cost, access to a large pool of developers | Performance can be an issue compared to native development, potentially less native-like UI/UX |
| Flutter | Excellent performance, high-quality UI/UX, hot reload feature for faster development | Smaller community compared to React Native, may require more specialized developers |
| Ionic | Faster development compared to native development, easy to use, and good documentation | Performance can be an issue, not as native-looking as React Native or Flutter |
| Native Development (iOS/Android) | Optimized performance, native-like user experience, greater control over device features | Higher development costs and time commitment, requiring separate teams for each platform |
Features and Functionalities of a Certify Compliance Mobile App
This mobile application empowers users to effortlessly manage and track their compliance obligations, transforming a potentially complex process into a streamlined experience. The intuitive design and robust features ensure compliance is not just met, but actively maintained.
This application’s key functionalities are designed to facilitate seamless compliance procedures, allowing users to manage documents, track progress, and generate reports – all from their mobile device. The secure data handling ensures confidentiality and integrity, while the user-friendly interface guarantees a positive experience for all stakeholders.
Essential Features for Streamlined Compliance Workflows
Streamlined workflows are crucial for efficient compliance management. This app offers several features to facilitate this, including automated reminders, pre-populated forms, and intuitive navigation. These features combine to minimize the time and effort required to maintain compliance.
- Automated Reminders: Automated reminders ensure timely submission of required documents, reducing the risk of penalties and maintaining compliance. These reminders are customized to individual user requirements, optimizing notification timing and avoiding redundant alerts.
- Pre-populated Forms: Pre-populated forms, based on company standards and regulatory requirements, speed up the process. This feature reduces the possibility of errors and ensures consistent compliance procedures.
- Intuitive Navigation: The app’s intuitive interface guides users through the various compliance tasks. Clear navigation menus and easy-to-understand instructions make the app user-friendly and accessible to all levels of expertise.
Secure Data Handling
Data security is paramount in a compliance application. The app employs industry-standard encryption methods to protect sensitive information, ensuring that user data remains confidential and inaccessible to unauthorized parties. This is crucial for maintaining trust and regulatory adherence.
“Data breaches can have severe consequences, including financial penalties, reputational damage, and legal ramifications. Robust security measures are therefore critical for a compliance mobile application.”
The app encrypts data both in transit and at rest, using strong encryption algorithms. This multi-layered approach safeguards sensitive information from potential threats. Regular security audits and updates further bolster the application’s security posture.
Document Upload and Management
Efficient document management is essential for maintaining compliance. The app offers a secure platform for uploading, organizing, and retrieving documents related to compliance obligations.
- Secure Upload: The app uses secure protocols for document uploads, preventing unauthorized access and ensuring data integrity.
- Organized Storage: Uploaded documents are organized logically, enabling easy retrieval and referencing based on specific criteria, such as date, type, or relevant regulatory requirements.
- Version Control: The app tracks document versions, enabling users to review previous versions and maintain an audit trail of changes.
Reporting and Tracking Compliance Status
Comprehensive reporting and tracking are vital for monitoring compliance progress. The app provides detailed reports on individual and overall compliance status, enabling proactive identification of potential issues and corrective actions.
- Real-time Tracking: The app allows for real-time monitoring of compliance status, enabling users to identify and address any deviations from the required procedures promptly.
- Customizable Reports: Users can generate custom reports to track specific aspects of their compliance obligations. This granular level of control enables users to tailor reports to their specific needs.
- Compliance Dashboard: The compliance dashboard offers a consolidated view of all compliance metrics and alerts, enabling a clear overview of the overall compliance status.
User Roles and Permissions
Different user roles require varying levels of access. The app’s granular permissions system allows administrators to control the access rights of different users.
| User Role | Permissions | Access Levels |
|---|---|---|
| Administrator | Full access to all features, user management, reporting | Highest |
| Compliance Officer | Access to specific compliance modules, document management, reporting | Medium |
| Employee | Limited access to relevant compliance tasks, document viewing | Lowest |
User Experience and Interface Design
Navigating complex compliance regulations can be daunting. A well-designed mobile app can significantly ease this process. Intuitive interfaces and seamless user flows are paramount for a positive user experience, ultimately fostering compliance and user satisfaction. This section explores best practices for designing mobile compliance apps, focusing on user needs and experience.
Best Practices for User Interface Design
Effective mobile compliance apps prioritize a clean, uncluttered interface that minimizes cognitive load. Users should be able to easily locate information and complete tasks without frustration. Clear visual hierarchy, consistent design elements, and appropriate use of color and typography contribute to a user-friendly experience. Consider using familiar patterns and conventions found in other popular mobile applications to increase user comfort and reduce learning time.
Design Considerations for Different User Groups
Different user groups may have varying needs and expectations. Consider these factors when designing your app:
- Compliance Officers: These users require quick access to key data points, reports, and regulatory updates. The interface should prioritize efficiency and allow for filtering and sorting of information to streamline their workflows. Detailed audit trails and comprehensive reporting options are essential.
- Employees: Employees need clear instructions and guidance for completing compliance tasks. Visual cues, interactive tutorials, and step-by-step guides are helpful for ensuring compliance and minimizing errors. The interface should be straightforward and easily navigable, minimizing the risk of misinterpretation or confusion.
- Administrators: Administrators need tools to manage user access, track compliance activities, and generate reports. Robust user management features, centralized dashboards, and customizable reporting options are crucial for administrators to oversee compliance effectively.
Importance of Clear and Concise Instructions
User manuals and in-app guides should clearly explain the purpose and functionality of each feature and task. Use simple, concise language, avoiding technical jargon whenever possible. Well-structured instructions, along with interactive walkthroughs, are crucial to guide users through the compliance process. Example: Instead of “Process document X using workflow Y,” use “Submit document X by following these steps.”
Examples of User Flows for Common Compliance Tasks
User flows illustrate the steps users take to complete common tasks. For instance, a user flow for submitting a document might involve: selecting the document, reviewing details, confirming submission, and receiving a confirmation message. These flows must be intuitive and logical. Detailed examples of user flows for tasks such as reporting incidents, updating employee information, or accessing policy documents are essential.
Mobile App UI/UX Patterns and Best Practices
Employing established mobile UI/UX patterns can greatly enhance user experience. Key patterns include:
- Navigation: Clear and consistent navigation menus are essential for users to find their way around the app.
- Input Fields: Input fields should be clearly labeled and provide feedback on input validity.
- Forms: Forms should be designed with a logical structure and clear instructions for completing each field.
- Error Handling: User-friendly error messages should guide users on how to correct mistakes.
Comparison of UI Styles
Different UI styles cater to various user preferences and needs. The following table compares various UI styles, highlighting their advantages and disadvantages:
| UI Style | Pros | Cons | Use Cases |
|---|---|---|---|
| Material Design | Visually appealing, consistent, and intuitive; responsive across devices. | Can be overly stylized for some users; may not suit all types of compliance apps. | General compliance apps with a wide range of users. |
| Flat Design | Clean and modern look; easy to customize and adapt to different brands. | Can appear simplistic and less visually engaging; might lack visual cues for complex tasks. | Apps requiring a clean, straightforward interface. |
| Minimalist Design | Focuses on functionality; removes unnecessary elements for a streamlined experience. | Can be challenging to navigate for users unfamiliar with the interface; might not suit apps with extensive features. | Compliance apps requiring efficient data access and management. |
Security and Data Privacy Considerations
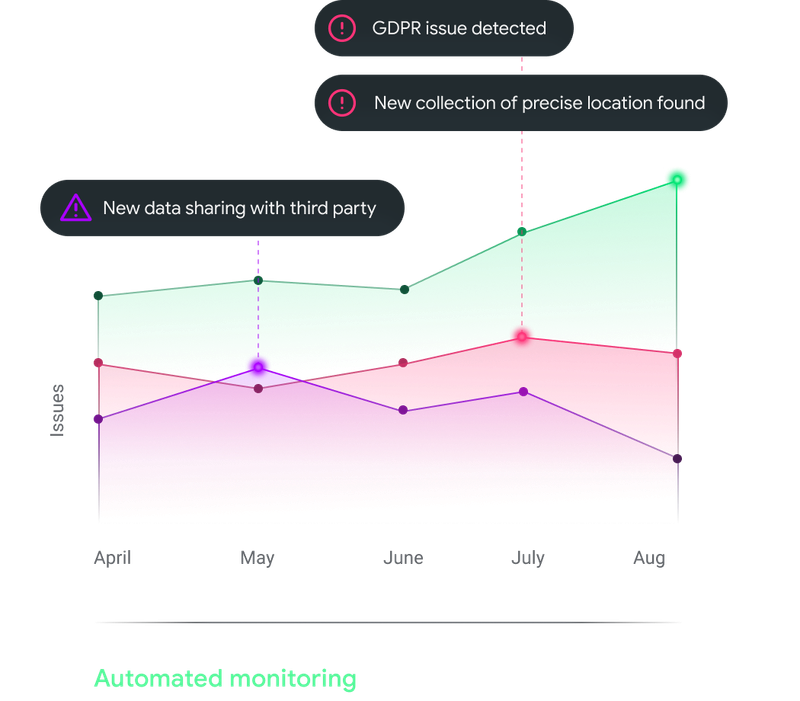
Fortifying the Certify Compliance mobile app against data breaches and ensuring user privacy is paramount. This section details the crucial security measures, encryption techniques, and compliance standards that underpin the app’s robust protection of sensitive user data. User trust is built on the foundation of secure practices, and we are committed to upholding the highest standards.
Data Encryption Methods
Protecting sensitive information, such as employee data, financial records, and regulatory compliance documents, is paramount in a mobile app. Robust encryption is essential to safeguarding this data during transmission and storage. The app will utilize Advanced Encryption Standard (AES) encryption, a widely recognized and secure algorithm. AES encryption, often implemented in 256-bit key length, provides strong encryption for sensitive data at rest and in transit. This method effectively scrambles data, making it unintelligible without the decryption key. Furthermore, the app will utilize Transport Layer Security (TLS) protocol to encrypt data transmitted between the mobile device and the Certify Compliance server.
Compliance with Relevant Data Privacy Regulations
The app will adhere to stringent data privacy regulations, including GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act). These regulations mandate that organizations collect, use, and store personal data responsibly. The app’s design will prioritize user control over their data. Features like data access, deletion, and restriction options will be prominently displayed, empowering users to manage their personal information effectively. Transparent data handling practices, Artikeld in the app’s terms of service and privacy policy, will be communicated clearly.
Secure Authentication Methods
Protecting user accounts from unauthorized access is critical. The Certify Compliance mobile app will employ multi-factor authentication (MFA) to enhance security. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile phone or email address. This layered approach makes it significantly harder for attackers to gain access to accounts, even if they obtain a user’s password. The app will leverage strong password policies, requiring complex passwords with a combination of uppercase and lowercase letters, numbers, and symbols. Regular security audits will ensure that the authentication methods remain robust against emerging threats.
Security Vulnerabilities and Mitigation Strategies
| Vulnerability | Description | Mitigation Strategy |
|---|---|---|
| SQL Injection | Attackers exploit vulnerabilities in SQL queries to gain unauthorized access to the database or manipulate data. | Parameterization of all SQL queries, input validation, and regular security audits. |
| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into web pages viewed by other users, potentially stealing sensitive data or redirecting users to fraudulent sites. | Input validation, output encoding, and employing secure coding practices. |
| Cross-Site Request Forgery (CSRF) | Attackers trick users into performing unwanted actions on a web application by exploiting vulnerabilities in the application’s session management. | Implementing CSRF tokens, validating user requests, and using secure headers. |
| Data breaches | Unauthorized access to sensitive data, potentially leading to data leaks and compromises. | Regular security audits, encryption of sensitive data at rest and in transit, and compliance with data privacy regulations. |
| Malware infections | Malicious software installed on user devices that compromises data or user accounts. | Employing robust antivirus software, educating users about potential threats, and regular software updates. |
Integration with Existing Systems

This Certify Compliance mobile app is designed to seamlessly integrate with your existing compliance management systems. This eliminates redundant data entry and ensures all your compliance information remains current and accurate across platforms. By connecting to your existing infrastructure, the app streamlines workflows, improving efficiency and reducing the risk of errors.
The app’s architecture is built with open APIs in mind, allowing for flexible and secure data exchange with various compliance management systems. This adaptability ensures the app can integrate with diverse tools, including ERP systems, CRM systems, and other specialized compliance platforms.
Data Exchange Process
The data exchange process between the mobile app and other systems is meticulously planned and executed. Data transfer occurs through secure, standardized protocols, ensuring data integrity and confidentiality. This process involves the secure transmission of relevant compliance documents, records, and status updates. Automated synchronization keeps all systems current, reducing manual intervention and minimizing potential errors. This is crucial for maintaining a comprehensive and accurate compliance record.
Benefits of Seamless Integration
Seamless integration with other tools offers significant advantages. It streamlines workflows, saving time and resources. Real-time data updates across systems improve visibility into compliance status. The elimination of manual data entry reduces the likelihood of errors and ensures data consistency. This leads to more accurate reports and informed decision-making. This enhanced efficiency is particularly valuable for organizations with multiple departments or complex compliance requirements.
Technical Requirements for Integration
Successful integration requires careful consideration of technical requirements. The app is designed with open APIs, facilitating connections with various systems. The app supports standard data formats, like JSON or XML, ensuring compatibility with most existing systems. Security protocols, including encryption and authentication mechanisms, are paramount to safeguard sensitive compliance data. Compatibility testing with potential integration partners is crucial to validate the integration’s functionality and ensure the app meets the technical specifications of each system.
Potential Integration Points
| System | Integration Method | Data Exchange |
|---|---|---|
| Enterprise Resource Planning (ERP) Systems | API integration | Automated transfer of employee data, relevant compliance documents, and audit trails. |
| Customer Relationship Management (CRM) Systems | API integration | Automated data synchronization of customer information and compliance requirements. |
| Document Management Systems | API integration or file sharing | Automated transfer of compliance documents, audit logs, and policies. |
| Compliance Management Software | API integration | Automated data synchronization of compliance records, policies, and training materials. |
| Third-Party Audit Platforms | API integration | Automated data exchange of audit results, corrective actions, and ongoing compliance status. |
Mobile App Development Considerations
Unleashing the power of mobile technology for Certify Compliance requires a meticulous approach to development. This phase focuses on selecting the optimal platform, ensuring robust technical specifications, and establishing a clear development process and testing strategy to deliver a seamless and secure user experience.
The Certify Compliance mobile application must not only be user-friendly but also highly functional, adhering to the highest security standards. This approach will guarantee a positive user experience and maintain the integrity of the compliance process.
Platform Selection and Strengths
Different mobile app development platforms offer varying strengths and weaknesses. Careful consideration of these factors is crucial for optimal application performance and user experience. Choosing the right platform directly impacts the app’s capabilities, cost, and scalability.
- Native Development (iOS and Android): Developing apps specifically for iOS and Android using native languages (Swift/Objective-C for iOS, Java/Kotlin for Android) results in applications that perform exceptionally well, integrate seamlessly with device features, and deliver a polished user experience. However, this approach requires separate development teams and codebases for each platform, increasing the project’s complexity and cost.
- Cross-Platform Development (React Native, Flutter): These frameworks allow developers to write code once and deploy it to multiple platforms (iOS and Android). This significantly reduces development time and costs compared to native development. However, the performance of cross-platform applications may not always match that of native apps, and the level of customization might be somewhat limited.
- Progressive Web Apps (PWAs): PWAs are web applications that can be installed on a user’s device and accessed like native apps. They are cost-effective and require minimal maintenance. However, their functionality may be constrained compared to native apps, and performance can vary depending on network connectivity.
Technical Specifications for a Robust App
The application must be built with specific technical considerations in mind to ensure scalability, reliability, and maintainability.
- Scalability: The application should be designed to handle a growing user base and increasing data volumes. This includes anticipating future demands and implementing robust database structures to avoid performance bottlenecks.
- Security: Implementing robust security measures is paramount. This includes encryption of sensitive data, secure authentication protocols, and adherence to industry best practices.
- Performance: The application should load quickly and respond promptly to user interactions. Optimized code, efficient data retrieval mechanisms, and caching strategies are crucial.
- Accessibility: The app should adhere to accessibility standards to ensure usability for users with disabilities. This includes features like screen reader compatibility and keyboard navigation.
Development Process and Timelines
A well-defined development process is crucial for delivering the application on time and within budget.
- Agile Methodology: Utilizing an agile development approach allows for iterative development, regular feedback, and adaptability to changing requirements. This methodology ensures the app meets the evolving needs of the users and stakeholders.
- Phased Rollout: A phased rollout strategy can minimize disruption and allow for continuous improvement. This approach allows for a gradual introduction of new features and functionalities, ensuring a smooth user experience.
- Realistic Timelines: Developing a realistic timeline is essential for effective project management. This requires careful consideration of all development stages, including design, development, testing, and deployment.
Testing Procedures for App Quality
Thorough testing is essential for ensuring a high-quality application.
- Unit Testing: Individual components of the application are tested to ensure their functionality and correctness.
- Integration Testing: Different components of the application are tested to ensure seamless interaction and data exchange.
- System Testing: The entire application is tested as a complete system to ensure it meets the overall requirements.
- User Acceptance Testing (UAT): Real users test the application to provide feedback on usability and functionality.
Key Technologies for Mobile App Development
Several key technologies are crucial for mobile app development.
- Programming Languages: Swift, Objective-C (iOS), Java, Kotlin (Android), JavaScript (Cross-Platform). The choice of language depends on the chosen platform and development framework.
- Databases: SQLite, Firebase Realtime Database, or other cloud-based databases can store and manage application data.
- Cloud Services: Cloud services like AWS, Azure, or Google Cloud Platform provide scalability and infrastructure support for the application.
- APIs (Application Programming Interfaces): APIs enable the app to integrate with external services and data sources, extending functionality.
Cost and Deployment Strategies
Navigating the financial landscape and deployment strategies for a mobile app is crucial for its success. Understanding the upfront costs, various deployment options, and ongoing maintenance is vital for a successful launch and long-term sustainability. This section Artikels the estimated costs, deployment methods, and maintenance strategies for the Certify Compliance mobile app.
The cost of developing and deploying a mobile app can vary significantly based on the features, complexity, and target platform. A thorough understanding of these factors is essential to accurately estimate the financial commitment and resources required for the project. Deployment strategies need to be tailored to the specific needs and resources of the organization.
Cost Estimation for Mobile App Development
The development of a Certify Compliance mobile app involves multiple stages, each with its own associated costs. Factors like the complexity of the features, the number of developers, and the choice of technologies all play a role in shaping the overall budget.
| Development Stage | Estimated Cost | Resources Required |
|---|---|---|
| Requirements Gathering & Design | $10,000 – $25,000 | Project manager, business analysts, designers |
| Development & Testing | $30,000 – $100,000+ | Software developers, QA testers, project managers |
| Deployment & Launch | $5,000 – $15,000 | App store submission specialists, marketing personnel |
| Post-Launch Support & Maintenance | Ongoing, $5,000 – $20,000+ per year | Technical support staff, developers |
Deployment Strategies
A variety of deployment strategies are available, each with its own advantages and disadvantages.
- Native Development: This approach involves developing separate apps for iOS and Android platforms. While offering a seamless user experience tailored to each platform, native development necessitates separate codebases for each, increasing development time and costs. However, native apps often achieve higher performance and better integration with device features.
- Cross-Platform Development (e.g., React Native, Flutter): These frameworks allow for the creation of apps for multiple platforms using a single codebase. This approach significantly reduces development time and costs compared to native development. However, the performance might be slightly less than native applications, and achieving optimal platform-specific functionality may require additional effort.
- Web App: This approach uses web technologies (HTML, CSS, JavaScript) to create an app that runs in a web browser. This deployment method often has lower initial development costs and requires fewer resources. However, the performance and user experience can sometimes be less optimal compared to native apps, especially in offline scenarios.
Pricing Models
Several pricing models can be employed for the Certify Compliance mobile app.
- Freemium: Offering a basic version of the app for free with premium features available for a subscription fee. This model can attract a large user base and generate revenue from premium features.
- Subscription-Based: Charging a recurring fee for access to the app and its features. This model provides a consistent revenue stream and encourages ongoing engagement.
- Pay-Per-Use: Charging for specific actions or features within the app. This model can be suitable for apps with a high volume of transactions or actions, such as compliance submissions.
Maintenance and Support
An effective maintenance and support plan is crucial for the longevity and stability of the Certify Compliance mobile app.
- Regular Updates: Addressing bugs, improving performance, and incorporating new features. This ensures the app remains secure, user-friendly, and aligns with evolving compliance standards.
- Technical Support: Providing assistance to users experiencing issues with the app. This can be achieved through various channels, such as email, FAQs, or dedicated support forums.
- Security Patches: Addressing vulnerabilities in the app’s code to prevent unauthorized access and data breaches. This is a critical aspect of maintaining user trust and compliance with data privacy regulations.
Epilogue
In conclusion, developing a mobile app for Certify compliance requires careful consideration of various aspects, from user experience and security to integration and cost-effectiveness. By understanding the features, functionalities, and design principles Artikeld in this guide, you can create a robust and user-friendly app that streamlines the compliance process and improves overall efficiency.