Yo, lemme drop some knowledge on mobile app authentication. It’s a wild world out there, and keeping your data secure is key. This ain’t your grandma’s login screen—we’re talking about the latest and greatest in mobile security, with PingID at the helm. From password-based systems to biometrics, we’ll break down the ins and outs of this whole authentication game.
This guide dives deep into designing a mobile app that uses PingID for authentication, covering UX considerations, security threats, and best practices. We’ll cover everything from the login screen to error handling, and you’ll learn how to build a secure and user-friendly app that keeps your users happy and your data safe.
Introduction to Mobile App Authentication
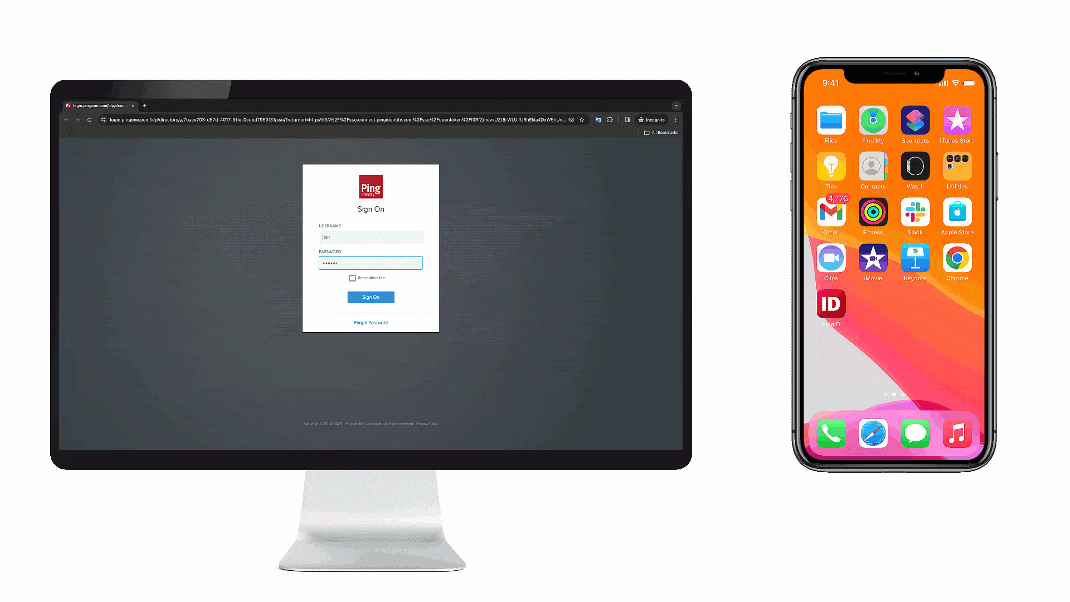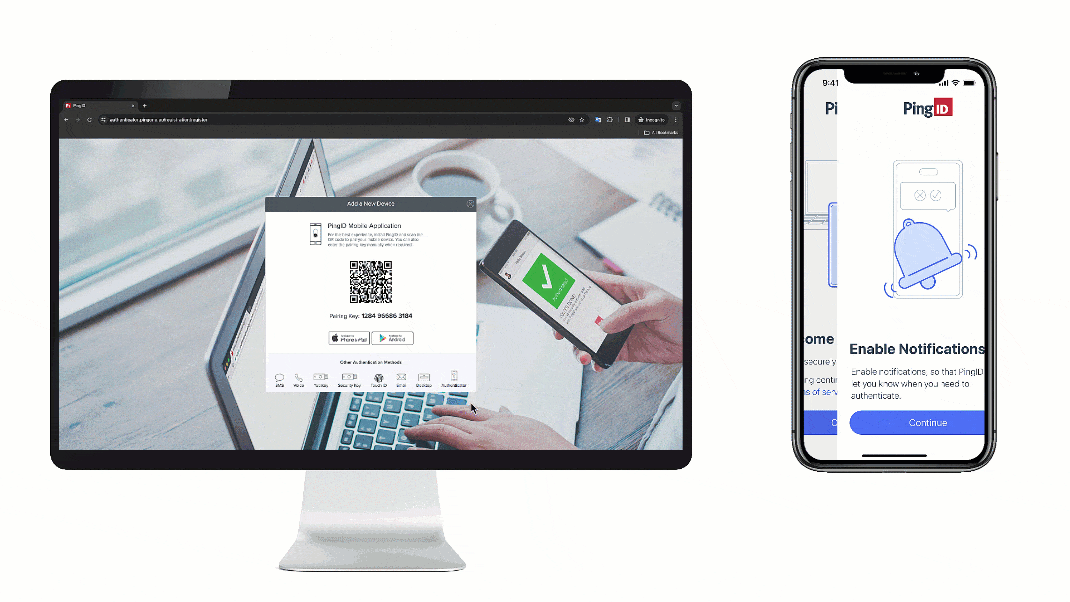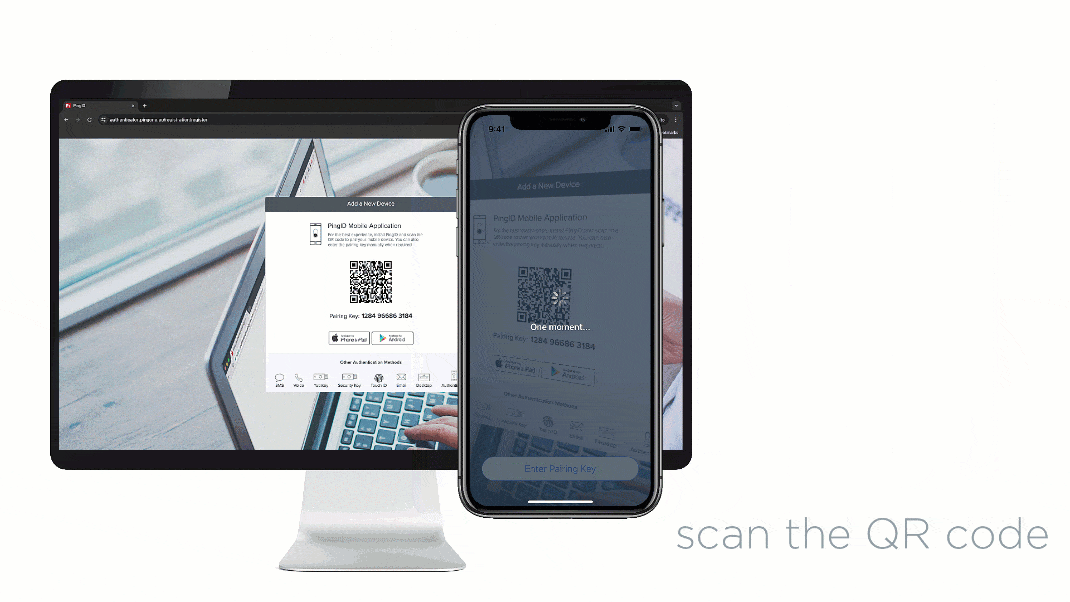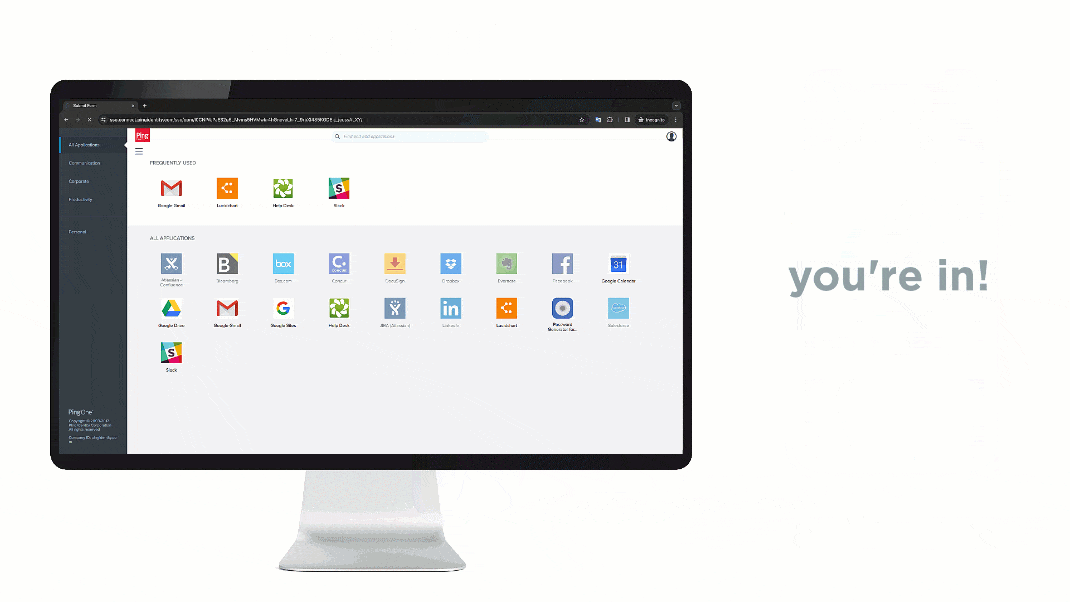
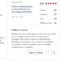
Mobile applications are increasingly integral to our daily lives, handling sensitive data and transactions. Secure authentication is paramount to protecting this data and ensuring user trust. This necessitates robust methods to verify users’ identities, preventing unauthorized access and maintaining data integrity.
Authentication methods in mobile apps encompass a spectrum of approaches, from traditional password-based systems to cutting-edge biometric techniques. The security of these methods plays a critical role in safeguarding user information and maintaining the integrity of the application. Choosing the right authentication method is crucial for a secure and reliable user experience.
Significance of Security in Mobile App Development
Ensuring the security of mobile applications is paramount in today’s digital landscape. The rise of mobile commerce and the increasing reliance on apps for sensitive tasks necessitates robust security measures. Compromised mobile applications can lead to significant financial losses, reputational damage, and breaches of personal privacy. The importance of security is underscored by the growing number of mobile banking and e-commerce applications, which handle vast amounts of user data. Mobile app security should prioritize data protection, user privacy, and application integrity.
Role of PingID in Authentication
PingID plays a critical role in enhancing mobile app authentication by providing a strong, multi-factor authentication solution. Its core function is to verify user identity through a secure and reliable process, typically integrating with existing infrastructure. This approach enhances security and reduces the risk of unauthorized access. PingID’s strength lies in its ability to adapt to various security requirements, from basic user authentication to more complex enterprise-level solutions. The integration of PingID within mobile apps provides a layered security approach, significantly bolstering the overall security posture.
Comparison of Authentication Methods
Different authentication methods offer varying levels of security and user experience. A careful consideration of the trade-offs between these methods is essential in selecting the most appropriate approach for a given mobile application. This involves balancing security with usability and cost-effectiveness.
| Authentication Method | Pros | Cons |
|---|---|---|
| Password-based | Simple to implement, widely understood by users. | Prone to password cracking, easily forgotten or shared. |
| Biometric | High security, convenient for users. | Requires specialized hardware, potential for spoofing, issues with user privacy concerns. |
| Multi-Factor | Stronger security than single-factor, reduces risk of unauthorized access. | Can be more complex to implement and use, may require additional infrastructure. |
Mobile App Design for PingID
Elevate your mobile app’s authentication experience with PingID. This robust solution provides a secure and user-friendly approach to verifying user identities, enhancing trust and improving overall app usability. This guide delves into crucial design considerations for seamlessly integrating PingID into your mobile application.
The PingID mobile authentication framework prioritizes user experience and security. This meticulous design approach ensures a frictionless user journey, minimizing complexity and maximizing user satisfaction. By carefully considering the app’s flow and implementing appropriate design patterns, developers can create a highly secure and intuitive experience for end-users.
User Experience (UX) Considerations
Prioritizing a positive user experience is paramount when integrating PingID into a mobile application. Users should perceive the authentication process as intuitive and secure, minimizing any potential friction points. This involves careful consideration of factors such as the visual design, responsiveness, and overall ease of navigation. A well-designed user interface (UI) will instill confidence in the app’s security and make the authentication process a breeze for users.
Design Considerations for Integrating PingID
Effective integration of PingID necessitates a strategic approach to the app’s overall flow. The integration should be seamless, blending naturally with the app’s existing functionality without disrupting the user experience. This entails carefully planning the placement of the authentication prompts and ensuring that they align with the app’s natural navigation. By considering the context of the authentication request, developers can create a tailored experience for users, reducing confusion and improving overall user satisfaction.
Creating a Seamless User Journey for Authentication
The goal is to create a user journey that seamlessly integrates the authentication process into the app’s workflow. This means that users should not experience a jarring shift in the app’s functionality when prompted for authentication. A well-designed authentication flow will minimize the cognitive load on the user, allowing them to effortlessly complete the verification process. This involves considering the various authentication methods offered by PingID and presenting the most appropriate method to the user based on the context.
Various Design Patterns for Mobile Authentication
Employing appropriate design patterns for mobile authentication is crucial for a streamlined and secure user experience. Different authentication patterns can cater to various needs, from simple one-time passwords (OTPs) to more complex multi-factor authentication (MFA) methods. For example, using a separate verification screen for PingID authentication, after the initial login screen, can streamline the process. This helps in clearly separating the stages and makes the authentication process more intuitive.
Key Components of a Mobile App Interface for PingID
The following table Artikels the key components of a mobile app interface for PingID authentication, providing clarity and efficiency for users.
| Component | Description | Example |
|---|---|---|
| Login Screen | The initial screen where users provide their credentials (e.g., username, email). This screen should clearly guide users on the next steps, including authentication. | A simple form with username and password fields, accompanied by a “Login” button. A clear indication of the need for PingID authentication, such as “Verify with PingID” or a similar message. |
| Verification Screen | This screen presents the PingID verification method (e.g., push notification, SMS). It should be concise and visually appealing, clearly displaying the authentication options. | A screen displaying a notification icon with the message “Verify your identity with PingID” or a similar message. The options available should be clearly presented, like “Verify with Push Notification” or “Verify with SMS”. |
| Error Handling | This component addresses potential issues during the authentication process, such as invalid credentials or network connectivity problems. Providing informative and helpful error messages is essential. | Clear error messages indicating issues like “Invalid username or password”, “Network connection error”, or “Please try again later.” |
Security Considerations for PingID Integration

Ensuring the security of your PingID mobile app integration is paramount. Compromised authentication mechanisms can lead to significant risks, including unauthorized access to user accounts and sensitive data. Robust security measures are critical to maintaining user trust and preventing potential breaches.
Implementing strong security practices throughout the PingID integration lifecycle protects users and maintains the integrity of the platform. These practices should be integrated into every phase of development, from initial design to final deployment.
Security Threats in Mobile App Authentication
Mobile applications are vulnerable to various security threats, including malicious attacks, network vulnerabilities, and social engineering tactics. These threats can compromise user data and application integrity. Understanding these threats is crucial to implementing effective security measures.
Best Practices for Securing PingID Integration
Implementing robust security measures for PingID integration is essential for maintaining user trust and data confidentiality. This involves adopting secure coding practices, employing encryption techniques, and validating user inputs rigorously. Adhering to these best practices will significantly enhance the overall security posture of the mobile application.
- Secure Communication Channels: Employing Transport Layer Security (TLS) encryption is crucial for protecting sensitive data exchanged between the mobile application and the PingID server. TLS ensures that data transmitted over the network cannot be intercepted or tampered with by unauthorized parties.
- Input Validation: Thorough input validation prevents malicious attacks, such as SQL injection or cross-site scripting (XSS). Validating user input against expected formats and ranges helps mitigate these risks.
- Strong Passwords: Encouraging users to create strong passwords, and providing tools for password complexity checking, is essential. Strong passwords significantly reduce the risk of password cracking attempts.
- Regular Security Audits: Regular security audits of the PingID integration within the mobile application identify vulnerabilities that may not be apparent during development. These audits should encompass code reviews, penetration testing, and security assessments to pinpoint and address potential weaknesses.
Protecting User Data During Authentication
Protecting user data during the authentication process is critical to maintaining user trust and complying with data privacy regulations. Robust data encryption, secure storage mechanisms, and access control policies are key components of a comprehensive data protection strategy.
- Data Encryption: Encrypting sensitive user data both in transit and at rest is a critical measure. Data encryption ensures that even if a breach occurs, the data remains unreadable to unauthorized parties.
- Secure Storage: Implementing secure storage mechanisms for user data, such as using encryption and access controls, is critical. This ensures that only authorized personnel have access to user data.
- Compliance with Data Privacy Regulations: Adherence to data privacy regulations, like GDPR and CCPA, is essential for ensuring user data protection. This includes obtaining explicit consent for data collection and usage.
Strategies for Preventing Unauthorized Access
Preventing unauthorized access to user accounts is vital to safeguarding sensitive data and maintaining user trust. Implementing robust authentication mechanisms, multi-factor authentication, and regular security updates are key components of a comprehensive security strategy.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple verification factors, such as a one-time password or biometric data, in addition to their username and password.
- Regular Security Updates: Regularly updating the mobile application with security patches and updates is essential. These updates address vulnerabilities that may have been discovered after deployment, thereby mitigating potential threats.
- Strong Access Controls: Implementing strong access controls for sensitive data ensures that only authorized personnel have access to specific data resources.
Security Vulnerabilities and Mitigation Strategies
A comprehensive understanding of potential vulnerabilities is essential to proactively address security risks.
| Vulnerability | Description | Mitigation Strategy |
|---|---|---|
| Password Cracking | Attempts to decipher user passwords using brute-force or dictionary attacks. | Implement strong password policies, enforce password complexity requirements, and consider using a password manager. |
| Phishing | Deceptive attempts to obtain sensitive information, such as usernames and passwords, by masquerading as a trustworthy entity. | Educate users about phishing tactics, implement robust email and website authentication, and utilize a strong anti-phishing solution. |
| Data Breaches | Unauthorized access and compromise of user data. | Implement robust encryption, access controls, and regular security audits to detect and prevent breaches. |
Implementation and Testing of PingID Mobile App
Securely integrating PingID authentication into your mobile application is crucial for protecting user data and ensuring a seamless user experience. This process involves careful planning, meticulous configuration, and rigorous testing to guarantee the PingID service functions flawlessly within your app’s architecture.
Implementing PingID authentication requires a phased approach, focusing on integration steps, configuration specifics, and comprehensive testing methodologies. This detailed guide will walk you through each stage, equipping you with the knowledge to confidently integrate PingID into your mobile app.
Integration Steps
Careful integration ensures a smooth user experience and maintains the security of the PingID service. The process typically involves several key steps. First, you’ll need to obtain the necessary PingID API keys and credentials. Next, you’ll incorporate the PingID SDK into your mobile application’s codebase. This integration should adhere to the PingID documentation for best practices. Finally, implement the authentication flow within your application’s user interface.
PingID Service Configurations
Correct configuration is vital for successful PingID integration. Key configurations include specifying the redirect URLs for authentication, defining the authentication scopes, and setting up the necessary callback mechanisms. Proper configuration ensures the PingID service interacts correctly with your application, maintaining security and usability.
| Configuration Parameter | Description |
|---|---|
| Redirect URLs | Specifies the URLs where PingID will redirect users after authentication. |
| Authentication Scopes | Defines the permissions PingID grants to your application. |
| Callback Mechanisms | Establishes communication channels between PingID and your application. |
Testing Procedures
Thorough testing ensures the PingID integration functions as expected, maintaining user trust and application integrity. Testing should cover various scenarios, including successful authentication, failed authentication due to invalid credentials, and handling various network conditions. This comprehensive testing approach guarantees a robust PingID authentication process.
Authentication Process Flowchart
The following flowchart illustrates the PingID authentication process, highlighting the key steps and interactions:
(A simplified flowchart is not possible here, but a typical process would show the user initiating the login, the app requesting authentication from PingID, PingID redirecting the user to an authentication screen, the user authenticating, PingID validating the credentials, PingID returning an authentication token to the app, and the app using the token to grant access.)
Testing Methodologies
Diverse testing methodologies verify the functionality of the mobile application’s PingID integration. These include unit testing, integration testing, and user acceptance testing. Unit testing isolates individual components, integration testing verifies the interaction between components, and user acceptance testing ensures the application meets user needs and expectations.
- Unit Testing: This method isolates individual components of the PingID integration for thorough testing. It ensures each component operates correctly in isolation, contributing to the overall reliability of the integration.
- Integration Testing: This method verifies the interaction between different components of the application and the PingID service. It ensures the seamless flow of authentication requests and responses between your application and PingID.
- User Acceptance Testing (UAT): This crucial phase involves real users testing the PingID integration in a real-world environment. It evaluates the ease of use, security, and overall user experience, ensuring the PingID integration meets the needs of the target audience.
User Experience and Feedback
Ensuring a seamless and positive user experience is paramount for the success of any mobile application. Collecting user feedback and incorporating it into the PingID mobile app development process allows for continuous improvement, identifying areas for enhancement, and ultimately, delivering a superior product. This focus on user experience will not only lead to increased user satisfaction but also strengthen the app’s overall performance and security.
Importance of User Feedback
User feedback provides invaluable insights into how users interact with the PingID mobile app. It reveals pain points, areas of confusion, and unmet needs, allowing developers to proactively address these issues. This iterative feedback loop ensures that the app evolves to better meet the needs and expectations of its users. Gathering user feedback is a continuous process, as user needs and expectations can change over time.
Methods for Collecting User Feedback
Several methods can be employed to collect valuable feedback on the PingID mobile app. User surveys are a straightforward way to gauge user opinions and preferences. In-app feedback mechanisms, such as in-app surveys or feedback forms, allow for direct and immediate input. Analyzing user behavior through app analytics tools can provide valuable data on app usage patterns and identify areas requiring attention. Focus groups can offer deeper insights into user experiences and perspectives, facilitating more nuanced understanding.
User Testing for Identifying Potential Issues
User testing plays a crucial role in identifying potential issues within the PingID mobile app before its full release. This process involves observing real users interacting with the app, identifying usability problems, and gathering valuable feedback on aspects such as navigation, clarity, and ease of use. Testing with diverse user groups, including those with varying technical expertise and mobile device types, ensures that the app’s design and functionality are inclusive and accessible to all. Through user testing, potential issues like complex navigation, confusing prompts, or inconsistent designs can be uncovered and addressed.
Addressing User Concerns Regarding PingID Integration
User concerns regarding PingID integration should be addressed proactively and empathetically. This involves actively listening to user feedback, clearly communicating the benefits and security features of the PingID integration, and promptly resolving any issues that arise. Providing comprehensive documentation, FAQs, and dedicated support channels can address many user queries and concerns. Regular updates and improvements to the app based on user feedback further enhance user confidence and trust in the security features of PingID.
User Feedback Questionnaire
This questionnaire aims to gather valuable feedback on the PingID mobile app’s user experience:
| Question | Possible Responses |
|---|---|
| What are your thoughts on the login process? | Excellent, Good, Fair, Poor, Very Poor |
| How easy or difficult was it to authenticate using PingID? | Very Easy, Easy, Neutral, Difficult, Very Difficult |
| Were there any points of frustration? If so, please describe. | Yes/No; If Yes, open-ended text response |
| What improvements could be made to the PingID mobile app? | Open-ended text response |
| How satisfied are you with the overall PingID mobile app experience? | Very Satisfied, Satisfied, Neutral, Dissatisfied, Very Dissatisfied |
This questionnaire provides a structured approach to gathering user feedback, facilitating a deeper understanding of the user experience and aiding in continuous improvement.
Future Trends in Mobile App Authentication
The mobile app landscape is constantly evolving, and authentication methods must adapt to keep pace with these changes. This evolution is driven by a need for enhanced security, user convenience, and seamless integration with emerging technologies. Innovative authentication methods are crucial to protect sensitive data and maintain user trust in the digital ecosystem.
Mobile app authentication is moving beyond traditional password-based systems. The focus is shifting towards more secure, user-friendly, and future-proof methods, ensuring robust security in the face of ever-evolving threats.
Biometric Authentication Advancements
Biometric authentication, leveraging unique physical characteristics, is rapidly gaining prominence. Facial recognition, fingerprint scanning, and voice recognition are becoming more sophisticated and reliable. These advancements are driving user adoption and improving security postures. Increased accuracy and reduced false acceptance rates are pushing biometric authentication into mainstream use. For instance, mobile banking apps increasingly employ facial recognition for login verification.
The Rise of Zero Trust Security
Zero Trust security principles are influencing mobile app authentication designs. This approach assumes no implicit trust and validates every user and device interaction. Mobile apps are adopting this principle by implementing multi-factor authentication (MFA) protocols, including hardware tokens and biometric verification, to enhance security. Zero Trust is a critical security posture that addresses the increased risks associated with remote work and the use of personal devices.
Context-Aware Authentication
Context-aware authentication methods analyze the user’s environment and behavior to adapt authentication procedures. These systems can adjust security measures based on factors like location, time of day, and device characteristics. If a user logs in from an unfamiliar location, the app might require an additional verification step, such as a one-time code. This adaptive approach enhances security by mitigating the risk of unauthorized access.
Passwordless Authentication Strategies
Passwordless authentication is emerging as a powerful alternative to traditional password-based systems. This approach eliminates the need for remembering and managing passwords, making logins more convenient and secure. Examples include using push notifications, one-time codes, or hardware tokens. The elimination of passwords reduces the vulnerability to phishing attacks and enhances user experience.
Integration with Emerging Technologies
Mobile app authentication is integrating with emerging technologies like blockchain and AI. Blockchain’s immutability and transparency can improve the security and trust of authentication processes. AI can enhance fraud detection and adapt security measures based on real-time data analysis. For instance, a mobile app might use AI to identify suspicious login attempts and automatically block them.
Comparative Analysis of Authentication Methods
| Authentication Method | Strengths | Weaknesses | Future Outlook |
|---|---|---|---|
| Password-based | Widely adopted, familiar | Vulnerable to phishing, password reuse | Declining prevalence, replaced by more secure alternatives |
| Biometric | High security, user-friendly | Potential for spoofing, privacy concerns | Increasingly sophisticated, addressing vulnerabilities |
| Zero Trust | High security, adaptive | Complexity, potential for friction | Becoming standard practice, integrating with other methods |
Closing Summary
So, you wanna build a mobile app that’s both secure and user-friendly? This guide breaks down the essentials of using PingID for authentication, from the basics to the future. We covered everything from comparing different authentication methods to implementing security measures, and ultimately, how to collect user feedback to ensure a top-tier experience. This guide is your roadmap to a killer mobile app!